This manual provides detailed information about the human-machine verification methods supported in the current system, including Alibaba Cloud Computing V1, GeeTest, Cloudflare, Alibaba Cloud Computing V2, etc. It also explains the configuration steps and related parameters for each verification method, aiming to assist users in successfully completing the human-machine verification configuration.
Alibaba Cloud Computing V1 GeeTest:
Corresponds to GeeTest:
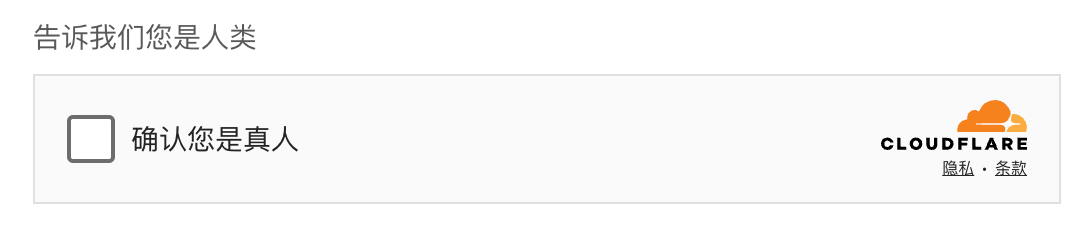
Cloudflare:
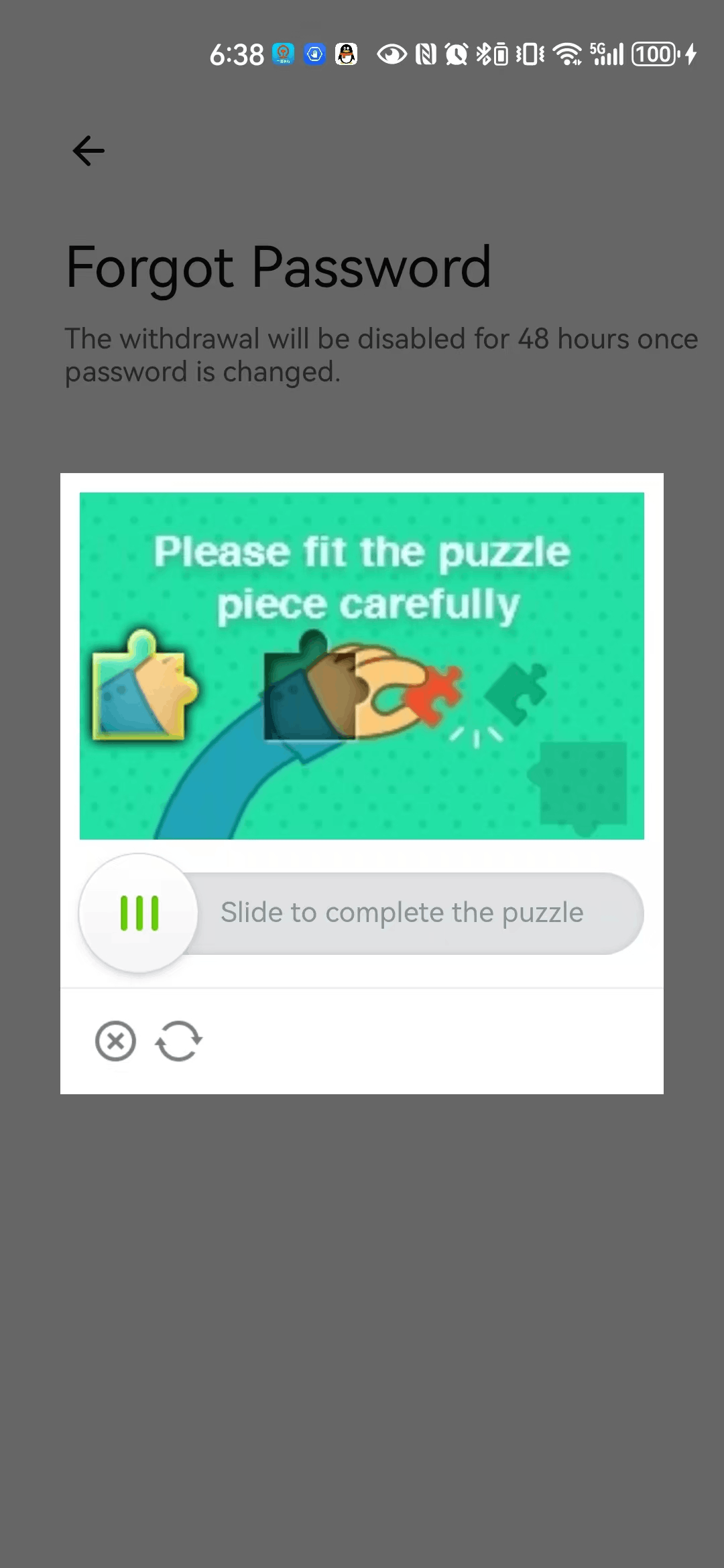
Corresponds to Alibaba Cloud Computing V2 GeeTest:
- Backend Operation Path: Operate in the backend and access the "Common Management - Common Configuration - KEY" page.
- APP Side Configuration
- Configuration Item: The key is app_sys_conf_validate.
- Value Explanation: The value has four options: 1, 2, 3, and 4. For types 3 and 4, the APP version needs to be upgraded to V6.2.3; otherwise, the APP will not support it. Type 2 will stop being used on January 31, 2025.
- PC&H5 Configuration
- Configuration Item: The KEY is sys_conf_validate.
- Value Explanation: The value has four options with the following specific meanings:
- 1: Corresponds to Alibaba Cloud Computing V1 GeeTest.
- 2: Corresponds to GeeTest. Note that it will stop being used on January 31, 2025.
- 3: Corresponds to Cloudflare (requiring a separate application for use), and the APP version needs to be upgraded to V6.2.3; otherwise, it is not supported temporarily.
- 4: Corresponds to Alibaba Cloud Computing V2 GeeTest, and the APP version needs to be upgraded to V6.2.3; otherwise, it is not supported.
- Backend Search Configuration Item: Search for sys_conf_cloudflare_config in the "Common Management - Common Configuration" section of the backend.
- Example of Configuration Parameter Format:
json
{
"site_key":"0x4AAAAAAA0_V9KQcJfaXU - T",
"secret_key":"0x4AAAAAAA0_V - xWigtofWv1Pb1NoCvBmdo"
}
- Application and Component Addition Steps: Go to https://dash.cloudflare.com/ca19ef0dba64f0b4676d6a402fa09e4e/turnstile/add to apply and add components.
- Before performing the configuration operation, ensure that you have a sufficient understanding of the current system and the relevant knowledge of the human-machine verification tool to avoid system failures or security issues caused by incorrect operations.
- When selecting configuration values for the APP side and PC&H5 side, be careful to set them according to actual requirements and system compatibility, especially for configuration items with version requirements, to avoid affecting the normal operation of the system.
- During the Cloudflare parameter configuration process, strictly follow the application and component addition process, ensure the accuracy of the obtained site_key and secret_key, and properly store the relevant information to prevent information leakage.